 A cyber-espionage group known as Turla — believed to be the cyber-arm of Russian intelligence — has been playing around with a backdoor trojan disguised as a Firefox extension that uses comments on Britney Spears Instagram photos to store the location of its command and control (C&C) server.
A cyber-espionage group known as Turla — believed to be the cyber-arm of Russian intelligence — has been playing around with a backdoor trojan disguised as a Firefox extension that uses comments on Britney Spears Instagram photos to store the location of its command and control (C&C) server.
Discovered in a recent distribution campaign by ESET researchers, this Firefox extension is part of a larger arsenal of hacking tools used by the Turla APT.
The group’s primary mode of operation is via compromised sites that load malicious code that forcibly download and execute malicious files on the user’s computer. This type of attack is known as a drive-by download and is used by exploit kits, malvertising campaigns, and cyber-espionage units.
Firefox extension distributed via hacked Swiss site
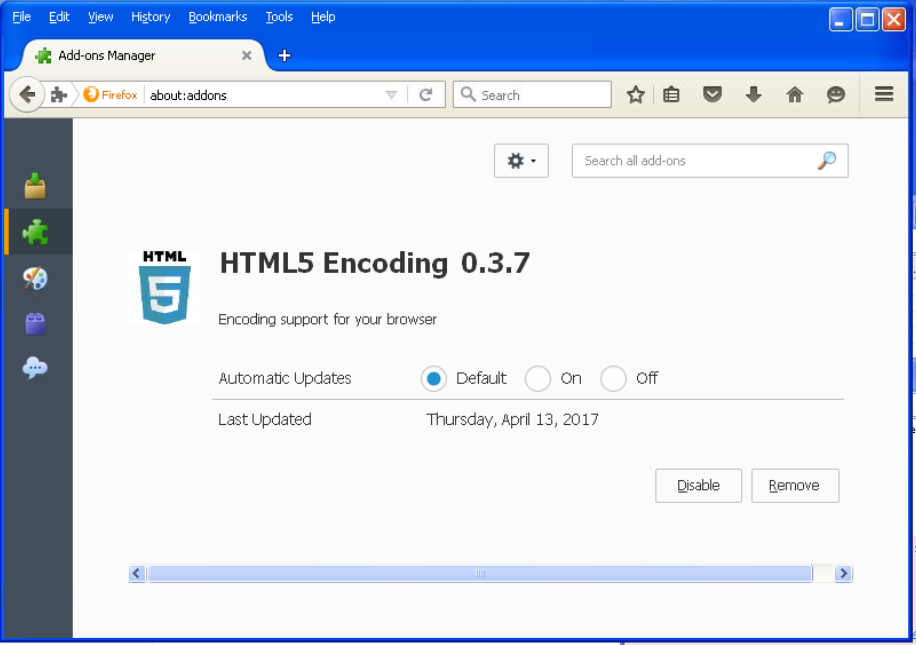
The Firefox extension is not installed by force, but researchers have seen it on the compromised site of a Swiss security company.
Visitors of this site were asked to install the extension, called HTML5 Encoding. ESET says this is a simple JavaScript-based backdoor that reports the user’s activity back to its operators.
 |
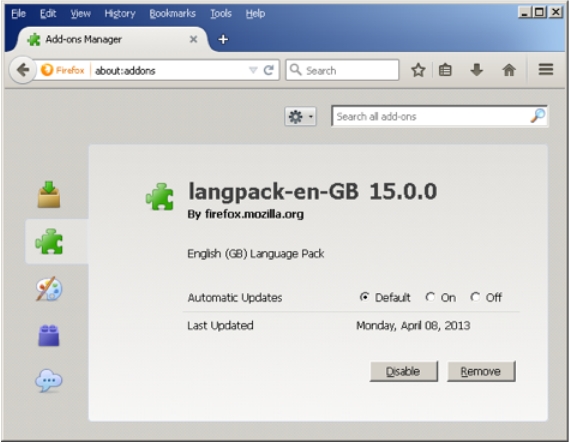 |
This wasn’t the first time researchers saw a Firefox extension delivering a backdoor. Back in July 2016, Bitdefender researchers discovered a new cyber-espionage unit — which they named Pacifier APT — that also used a Firefox extension to install backdoors on user’s devices.
That Firefox extension, named langpack-en-GB, used a different tactic, as it employed macro-laced Word files that asked the user to install the extension.
When they took a closer look at Bitdefender’s findings, ESET researchers realized that the Firefox extension was downloading a version of the Skipper backdoor, a known Turla malware family. As the Skipper malware is unique to Turla, this means that the Pacifier campaign that targeted Romanian government institutions was most likely the work of the Turla APT.
Using Instagram photos to encode C&C server URL
While the first Firefox extension was actively deployed in a cyber-espionage campaign, ESET researchers say this second one, named HTML5 Encoder, appears to be only a test.
They say this because the Firefox extension used a C&C server URL that resolved through a Bit.ly short URL, which allowed researchers to detect how many times the URL was accessed. According to the ESET team, this was only 17 times at the time they discovered it, meaning the extension was barely used.
But the weirdest thing wasn’t that they’ve discovered a backdoor hidden inside a rarely used Firefox extension. The most surprising thing is how the extension resolved its C&C server domain.
According to ESET, the malware would connect to the comments section of a photo uploaded on Britney Spears’ Instagram account and search for a comment that had a hash with the value 183.
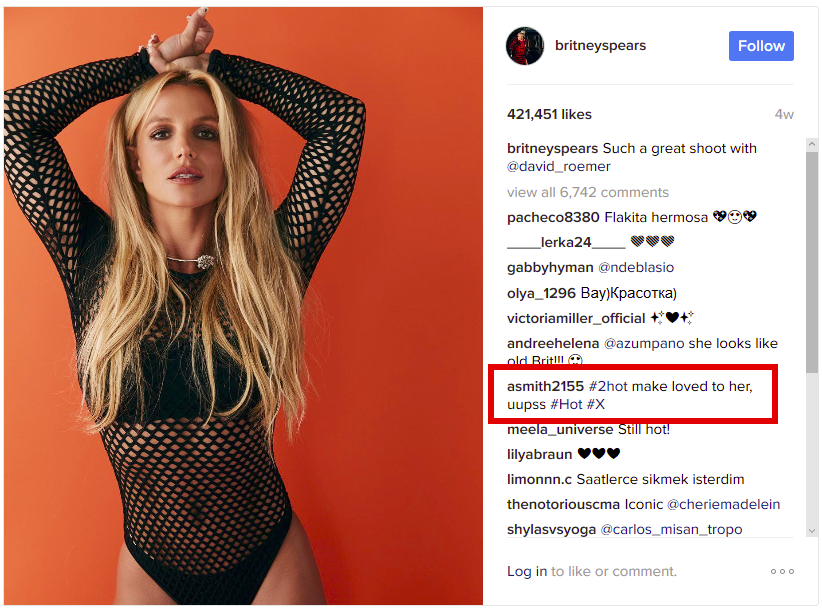
Researchers say that only one comment had that hash value, and that comment contained hidden characters that were used to resolve the C&C server domain. Below is ESET’s explanation for how the malware resolved the C&C domain:
Looking at the photo’s comments, there was only one for which the hash matches 183. This comment was posted on February 6, while the original photo was posted in early January. Taking the comment and running it through the regex, you get the following bit.ly URL:
http://bit.ly/2kdhuHX
Looking a bit more closely at the regular expression, we see it is looking for either @|# or the Unicode character \200d. This character is actually a non-printable character called ‘Zero Width Joiner’, normally used to separate emojis. Pasting the actual comment or looking at its source, you can see that this character precedes each character that makes the path of the bit.ly URL:
smith2155< 200d >#2hot ma< 200d >ke lovei< 200d >d to < 200d >her, < 200d >uupss < 200d >#Hot < 200d >#X
When resolving this shortened link, it leads to static.travelclothes.org/dolR_1ert.php , which was used in the past as a watering hole C&C by the Turla crew.
ESET says this Firefox extension contained some pretty intrusive features, allowing the Turla crew to read a directory’s content, download and upload files from and to the C&C server, and execute files on the infected machine. These are basic features, compared to more powerful backdoors, but they are more than enough for a skilled attacker.
The good news is that this attack vector will soon be deprecated. By the end of the year, Firefox plans to move away from the old NPAPI Add-ons API to a newer API called WebExtensions.
Both Turla Firefox extensions were created on old NPAPI-based technologies. The new WebExtensions API doesn’t provide the same level of interaction with the underlying OS.
Visitas: 133
